Security and robustness of your software applications are more important than ever since the malice of cyberattacks and the complexity of software vulnerabilities has risen considerably. While traditional testing methods can help you detect bugs, they may not cover all the unexpected edge cases or vulnerabilities that malicious objects could exploit. That’s where fuzz testing comes into play.
In this blog, we’ll explore fuzz testing, a powerful technique to uncover hidden bugs and security flaws. We’ll discuss its benefits, how it works, the bugs it identifies, and more. Read along to find out.
What is Fuzz Testing?
Fuzz testing, often called fuzzing, is an automated software testing technique that feeds random, unexpected, or malformed data into a program to expose vulnerabilities and bugs. The primary goal of fuzz testing is to provoke crashes or abnormal behavior in your application, revealing security flaws, input handling issues, and system instability.
Fuzz testing is particularly effective at identifying bugs that might be difficult to detect using traditional testing methods, such as unit testing or integration testing. By simulating unexpected inputs, you can uncover issues that could lead to severe security vulnerabilities in your software.
History of Fuzz testing
You might find it interesting that Professor Barton Miller at the University of Wisconsin-Madison introduced fuzz testing in 1988. Originally aimed at testing the robustness of Unix programs, fuzz testing has evolved significantly over the years. Today, it includes more sophisticated fuzzing tools and automated workflows that make it widely used across various industries to identify previously unknown vulnerabilities.
Benefits of Fuzz Testing
Fuzz testing offers a multitude of benefits that significantly enhance the quality and security of your software application:
Early Detection of Vulnerabilities
One of the most significant benefits of fuzz testing is its ability to identify security flaws and stability issues early in the development cycle. By exposing your application to a wide range of unexpected inputs, fuzz testing allows you to discover vulnerabilities before they are moved to production.
Early detection is crucial because it not only reduces the risk of security breaches but also minimizes the time and cost associated with fixing these issues later in the development process. This proactive approach enables you to maintain a more secure application from the outset.
Comprehensive Coverage
Fuzz testing is designed to test a wide array of input scenarios, including edge cases that might not be covered by traditional testing methods. Traditional testing often focuses on a limited set of expected inputs, which can lead to gaps in coverage.
Fuzz testing, on the other hand, injects random, malformed, or unexpected data into your application, exploring areas that might otherwise go untested. This comprehensive approach ensures that you are evaluating your application under various conditions, enhancing its robustness and reliability.
Automation and Efficiency
Another major advantage of fuzz testing is its ability to automate the testing process. Fuzz testing tools can quickly generate and execute large volumes of test inputs automatically, saving you significant time and effort.
This level of automation allows you to run tests continuously and at scale, making it easier to identify issues across multiple iterations of your software. As a result, you can focus your resources on fixing vulnerabilities rather than spending excessive time on manual testing, thereby streamlining your development workflow.
Identification of Complex Bugs
Fuzz testing excels at uncovering subtle and hard-to-find bugs, particularly those related to memory management and concurrency. Traditional testing methods may struggle to identify issues such as buffer overflows, race conditions, or memory leaks.
Fuzz testing systematically injects a variety of inputs, often exposing complex bugs that could lead to application crashes or unexpected behaviors. By identifying these issues early, you can improve the overall stability and performance of your application.
Improved Security Posture
Implementing fuzz testing as part of your testing strategy significantly strengthens your application’s security posture. By proactively identifying potential vulnerabilities, you can address security flaws before they can be exploited by malicious actors.
This not only protects your application from attacks but also helps you comply with industry standards and regulations regarding data security. A robust security posture instills confidence in your users and stakeholders, ensuring that their data is safe and your application is reliable.
Enhanced Reliability and Stability
Fuzz testing contributes to enhanced reliability and stability by reducing the likelihood of crashes and unexpected behaviors in your software. By identifying and fixing issues before they reach production, you can ensure a smoother user experience and decrease the chances of critical failures. This reliability is particularly important for applications that handle sensitive data or are mission-critical, as even minor disruptions can have significant repercussions.
Cost-Effective Testing
Incorporating fuzz testing into your testing regimen can lead to substantial cost savings over time. By catching vulnerabilities and bugs early in the development process, you can reduce the overall testing and maintenance costs associated with your application.
Fixing issues in the early stages of development is typically much less expensive than addressing them after they have been discovered in production. This cost-effective approach allows you to allocate your resources more efficiently, ultimately leading to a better return on investment.
Continuous Integration and Testing
Fuzz testing integrates seamlessly into Continuous Integration/Continuous Deployment (CI/CD) pipelines, enabling regular, automated quality checks throughout the development cycle. By incorporating fuzz testing into your CI/CD process, you can ensure that your application is continuously monitored for vulnerabilities, allowing you to catch issues as they arise.
This integration supports a culture of quality within your development team and helps maintain high standards for software reliability and security over time.
How Fuzz Testing Work?
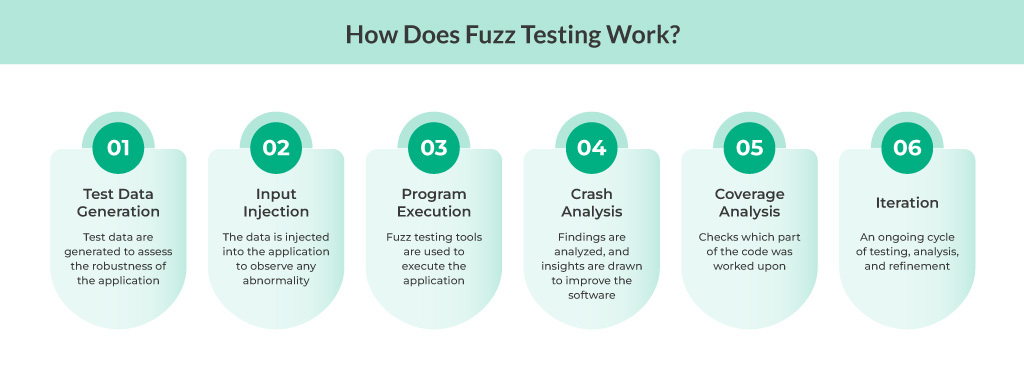
Fuzz testing is a sophisticated technique designed to expose vulnerabilities and bugs in software applications by feeding them unexpected or malformed input data. Understanding how fuzz testing works is crucial for effectively implementing it in your software development lifecycle. Here’s a detailed look at the key processes involved in fuzz testing:
1. Test Data Generation
The first step in fuzz testing is generating test data that will be used to assess the robustness of your application. There are various approaches to generating this data:
- Random Generation: This method creates completely random inputs without regard to the expected format. While it can uncover unexpected behaviors, it may not effectively explore all input scenarios.
- Mutation-Based Generation: In this approach, existing valid inputs are modified (or “mutated”) to create new test cases. This allows the fuzz tester to explore how small changes in input affect the application’s behavior.
- Template-Based Generation: This method uses templates based on the expected input formats of the application, creating inputs that conform to specific structures or protocols. This approach can be particularly effective for applications with well-defined input formats.
By employing these techniques, fuzz testing tools can generate a wide array of inputs to thoroughly evaluate the application’s handling of unexpected data.
2. Input Injection
Once the test data is generated, the next step involves injecting this data into the application being tested. This can be accomplished in several ways, depending on the nature of the application:
- API Calls: If the application has an API, the fuzz tester can send the generated inputs through API requests, allowing for comprehensive testing of the application’s backend.
- User Interface Interactions: For applications with a graphical user interface (GUI), fuzz testing can simulate user interactions by injecting inputs directly into form fields or input controls.
- File Uploads: Some applications accept files as inputs. Fuzz testing can involve uploading malformed or unexpected files to see how the application handles them.
The goal during this stage is to evaluate how well the application processes the injected data and to observe any deviations from expected behavior.
3. Program Execution
After input injection, the fuzz testing tool executes the application with the provided inputs. During this execution, the tool closely monitors the application’s behavior for any signs of failure or abnormality. Key aspects to observe include:
- Crashes: Any unexpected termination of the application is recorded, as it may indicate a critical flaw.
- Resource Utilization: Monitoring CPU and memory usage can help identify potential memory leaks or excessive resource consumption.
- Logs and Outputs: The application’s output and any error logs generated during execution are captured for analysis.
This stage is crucial for collecting data on how the application behaves under stress and unexpected conditions.
4. Crash Analysis
If the application crashes or exhibits abnormal behavior during program execution, the next step is to perform a crash analysis. This analysis involves:
- Reproducing the Crash: The specific input that caused the crash is noted, and attempts are made to reproduce the issue consistently. This helps confirm that the crash is indeed a legitimate vulnerability.
- Debugging: Developers and testers use debugging tools to analyze the application’s state at the time of the crash. This may involve examining stack traces, memory contents, and variables to understand the underlying cause of the failure.
- Identifying Vulnerabilities: By analyzing the crash, testers can determine whether it relates to security vulnerabilities (e.g., buffer overflows) or logical errors in the code.
This stage is essential for translating the findings from fuzz testing into actionable insights for improving the software.
5. Coverage Analysis
After executing multiple fuzz tests, it is vital to conduct coverage analysis. This involves assessing which parts of the code were exercised during testing and which were not. Key elements of coverage analysis include:
- Code Coverage Metrics: Tools can provide metrics on line coverage, branch coverage, and function coverage to determine how much of the codebase has been tested.
- Identifying Gaps: By analyzing the coverage data, you can identify areas of the application that may require additional testing or refinement in your fuzzing strategy.
- Guiding Future Tests: Coverage analysis helps inform the generation of new test inputs to maximize the exploration of the codebase, ensuring that previously untested paths are evaluated.
This iterative feedback loop is critical for refining the fuzz testing process and ensuring thorough application testing.
6. Iteration
The final step in the fuzz testing process is iteration. Fuzz testing is not a one-time event but rather an ongoing cycle of testing, analysis, and refinement. This involves:
- Refining Test Cases: Based on the findings from crash and coverage analyses, new test inputs can be generated to explore untested areas of the application or to probe more deeply into specific vulnerabilities.
- Continuous Monitoring: As you develop and modify your application, continuous fuzz testing can help ensure that new changes do not introduce additional vulnerabilities.
- Integration with CI/CD: By integrating fuzz testing into your Continuous Integration/Continuous Deployment (CI/CD) pipeline, you can automate the process of running fuzz tests on a regular basis, ensuring ongoing quality assurance as the application evolves.
Iteration in fuzz testing ensures that your application remains robust and secure throughout its lifecycle, addressing new vulnerabilities as they arise.
What Bugs are uncovered in Fuzz Testing?
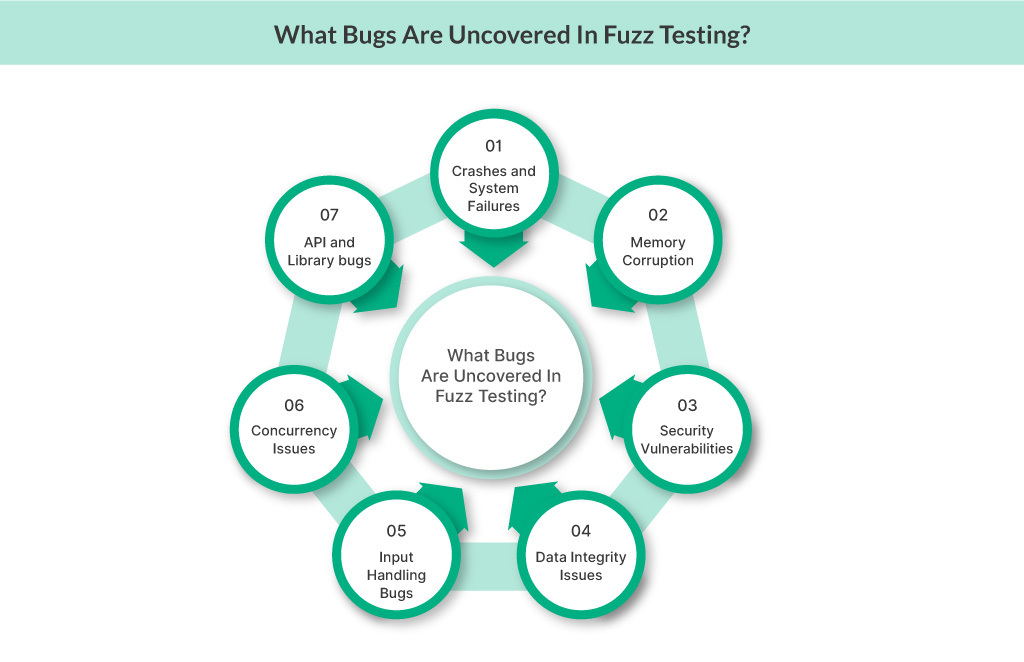 Fuzz testing is instrumental in identifying various bugs and vulnerabilities within software applications. Here’s a brief overview of some common issues that fuzz testing can help uncover:
Fuzz testing is instrumental in identifying various bugs and vulnerabilities within software applications. Here’s a brief overview of some common issues that fuzz testing can help uncover:
Crashes and System Failures
Fuzz testing often reveals application crashes and system failures caused by unhandled exceptions or critical errors when unexpected inputs are processed. These crashes can disrupt user experience and indicate underlying stability issues.
Memory Corruption
Memory corruption bugs, such as buffer overflows and use-after-free errors, occur when an application incorrectly manages memory allocation. Fuzz testing can identify these vulnerabilities, which can lead to unpredictable behavior, data leaks, or security exploits.
Security Vulnerabilities
Fuzz testing uncovers various security vulnerabilities, including input validation errors and injection attacks. By exposing weaknesses in how an application handles malicious input, fuzz testing helps strengthen overall application security against potential threats.
Data Integrity Issues
Fuzz testing can identify data integrity issues, such as data corruption and race conditions, which occur when input is not processed or stored correctly. These issues can lead to inconsistencies and unreliable data within the application.
Input Handling Bugs
Input handling bugs arise when an application fails to properly process unexpected or malformed input, resulting in unhandled exceptions or incorrect parsing. Fuzz testing exposes these bugs, ensuring that applications can robustly handle a wide range of input scenarios.
Concurrency Issues
Concurrency issues, such as race conditions and deadlocks, are often revealed through fuzz testing, especially in multi-threaded applications. These bugs occur when simultaneous operations conflict, leading to unpredictable behaviors and application freezes.
API and Library Bugs
Fuzz testing is effective in identifying bugs in APIs and third-party libraries, including protocol violations and vulnerabilities within external components. This helps ensure that applications interact correctly with external dependencies and maintain security and stability.
Different Types of Fuzz Testing
Fuzz testing includes several types, each with its own way of generating inputs and finding vulnerabilities.
Mutation-Based Fuzzing
In mutation-based fuzzing, you take valid inputs and slightly change them to create new test cases. This helps you check how the application handles unexpected input and uncovers flaws in its processing logic.
Random Fuzzing
With random fuzzing, you generate completely random inputs without thinking about the expected format. This approach helps you discover unexpected edge cases and vulnerabilities, though it may sometimes produce irrelevant results.
Coverage-Guided Fuzzing
Coverage-guided fuzzing uses code coverage information to guide your input generation. By focusing on areas of the code that haven’t been tested yet, you maximize your chances of finding vulnerabilities.
Behavioral Fuzzing
Behavioral fuzzing targets specific application behaviors to find weaknesses. By understanding how the application is typically used, you can create test cases that mimic real-life scenarios, making it more likely to uncover critical flaws.
Generation-Based Fuzzing
In generation-based fuzzing, you create new inputs from scratch based on known input formats. This is useful for applications with complex data structures, ensuring that your tests are relevant and effective.
Smart Fuzzing
Smart fuzzing uses your knowledge of application logic and past vulnerabilities to generate targeted test cases. This approach helps you focus on inputs that are more likely to reveal weaknesses in the application.
File Format Fuzzing
File format fuzzing checks how applications handle malformed or unexpected files. This is essential for applications that process files, helping you identify vulnerabilities related to file parsing and data handling.
Intelligent Fuzzing
Intelligent fuzzing combines different strategies to generate effective test inputs. By using insights from various fuzzing techniques, you can improve your testing process and explore the application more thoroughly.
Tools for Fuzz Testing
- AFL (American Fuzzy Lop): A powerful, mutation-based fuzzing tool that instruments the target program to provide feedback on code coverage.
- LibFuzzer: A library for in-process fuzzing, mainly used in combination with sanitizers like AddressSanitizer to find memory-related bugs.
- Peach Fuzzer: A commercial fuzzing platform that supports a wide range of protocols and file formats.
- Google OSS-Fuzz: An open-source fuzzing service that integrates with continuous integration (CI) to automatically find bugs in open-source software.
- Google ClusterFuzz: The fuzzing engine used by Google to check for bugs in Chrome. It’s also part of the backend for the OSS-Fuzz project. It works with any program or application.
Challenges of Fuzz Testing
While fuzz testing is a powerful technique for identifying vulnerabilities, it also presents several challenges that can affect its effectiveness. Here’s an overview of some common challenges, along with potential solutions:
False Positives
One of the primary challenges of fuzz testing is the occurrence of false positives, where the tests indicate a vulnerability that does not actually exist. This can lead to wasted time and resources investigating non-issues.
Implementing a rigorous validation process, including manual code reviews and additional testing methods, can help filter out false positives and focus on genuine vulnerabilities.
Input Generation Complexity
Generating effective test inputs can be complex, particularly for applications with intricate data formats or protocols. It’s often challenging to create inputs that thoroughly explore the application’s behavior under various conditions.
Utilizing more advanced input generation techniques, such as coverage-guided fuzzing, can improve the effectiveness of input generation by focusing on untested paths in the code.
Resource Intensive
Fuzz testing can be resource-intensive, requiring significant computational power and time to execute large volumes of tests. This can be particularly problematic for larger applications with extensive codebases.
Optimizing the fuzz testing process, such as parallelizing tests and using cloud resources, can help manage resource demands and improve efficiency.
Coverage Gaps
Fuzz testing may not achieve complete code coverage, meaning some parts of the application could remain untested. This can leave critical vulnerabilities undetected.
Combining fuzz testing with other testing techniques, such as unit tests and integration tests, can help ensure broader coverage and reduce the risk of missing vulnerabilities.
Reproducibility Issues
Reproducing the conditions that led to a vulnerability can be difficult, making it challenging to analyze and fix the identified issues. This is especially true if the input data is random or if specific application states are needed.
Implementing logging and capturing detailed execution traces during fuzz testing can help recreate the scenarios in which vulnerabilities were discovered, facilitating easier analysis and debugging.
Performance Overhead
Fuzz testing can introduce performance overhead to the application being tested, potentially affecting its responsiveness during the testing process. This can be particularly concerning in production environments.
Running fuzz tests in controlled environments or using staging servers can minimize the impact on production systems while still allowing for thorough testing.
Tool Limitations
Not all fuzz testing tools are created equal; some may lack features or capabilities necessary for specific applications, limiting their effectiveness. This can result in incomplete testing and undetected vulnerabilities.
Researching and selecting the right fuzz testing tools that best fit your application’s requirements and integrating them into your testing workflow can enhance effectiveness.
Complex Error Diagnosis
When fuzz testing uncovers a bug, diagnosing the root cause can be complex. The random nature of fuzzing may make it difficult to pinpoint why a particular input caused a failure.
Employing robust error analysis tools and techniques can help streamline the diagnosis process, making it easier to identify the underlying issues related to the detected bugs.
Final Thoughts
Fuzz testing is a powerful and efficient way to uncover software application bugs and security vulnerabilities. Its ability to generate unexpected inputs and test edge cases that traditional testing may not cover makes it an essential tool for developers and QA testers. By integrating fuzz testing into your CI/CD pipelines, you can catch issues early, strengthen application security, and enhance the overall reliability of your software.
QA Touch streamlines your testing efforts with its comprehensive suite of test management tools, including support for automated testing workflows. Start improving your testing process today!
Ready to streamline your testing efforts? So start your 14-day free trial today.







